The Irony of Trust: Analyzing a "Data Blocker" from a Cyber Conference
Introduction
I recently attended CyberCon 2025 in Melbourne, where NAB (National Australia Bank) was handing out USB “data blocker” devices as promotional items. The irony wasn’t lost on me: at a cybersecurity conference, attendees were being given opaque, sealed USB devices and expected to trust them.
In an era of sophisticated hardware attacks—from O.MG cables to USB Rubber Duckies—accepting unknown USB devices seems contrary to basic security hygiene. These data blockers come in sealed black casings that prevent visual inspection without destruction, containing ample internal space that could theoretically house malicious payloads.
Curiosity got the better of me. I decided to crack one open and analyze what’s actually inside.
What Is a USB Data Blocker?
A USB data blocker (also called a “USB condom” or “juice-jack defender”) is a simple adapter designed to allow charging while preventing data transfer. The concept is straightforward: block the data lines, pass through the power lines.
This NAB device is a USB Type-A male to USB Type-C female adapter, allowing you to plug it into a USB-A port (like a public charging kiosk) and then connect your USB-C device for “safe” charging.
The Hardware Analysis
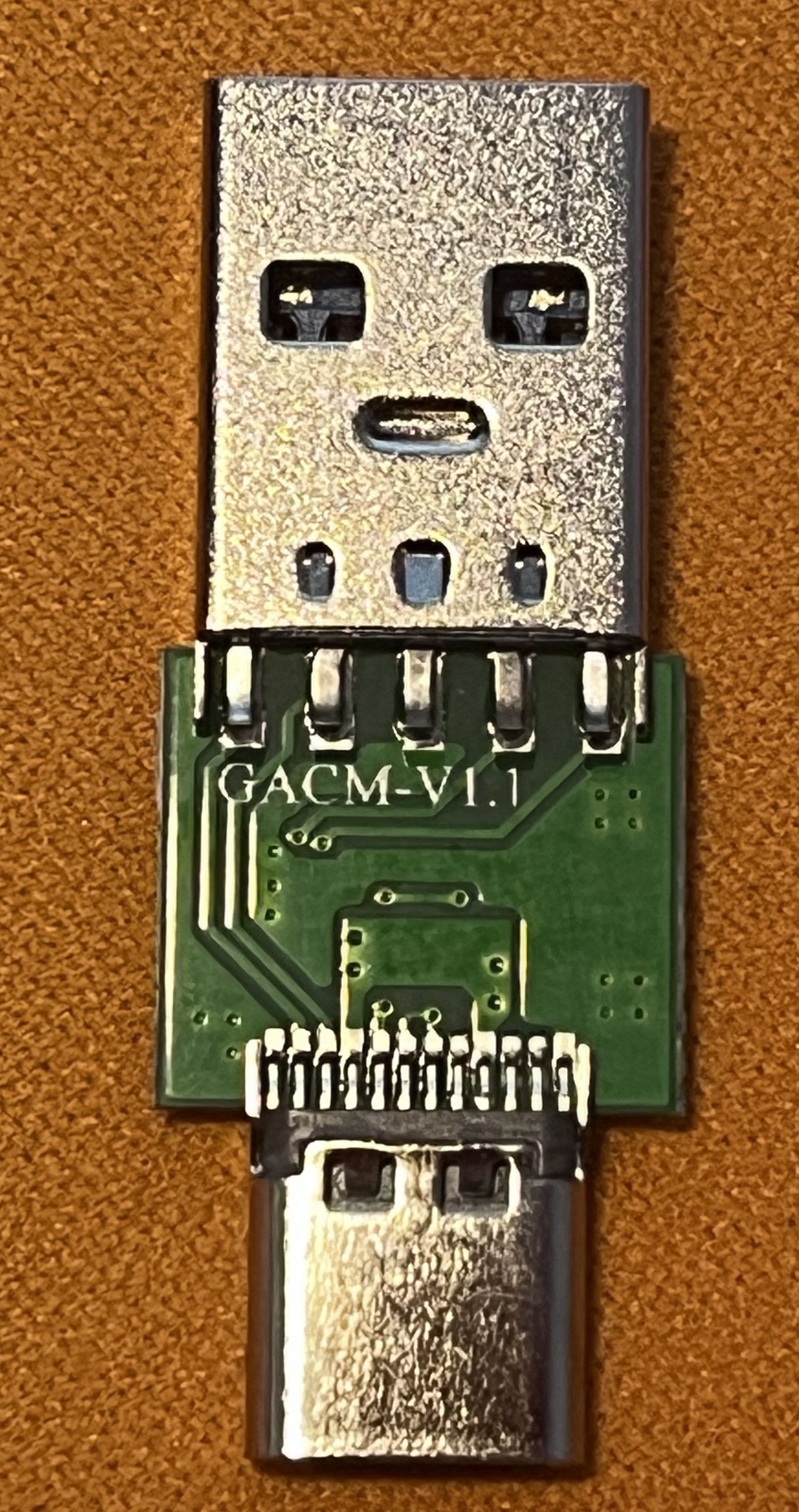
After carefully opening the sealed casing, I examined the PCB and traced the connections. Here’s what I found:
The PCB appears to have the marking GACM-V1.1 but I was unable to find any further information on this, so the next logical step is to review each PCB trace and reverse engineer it!
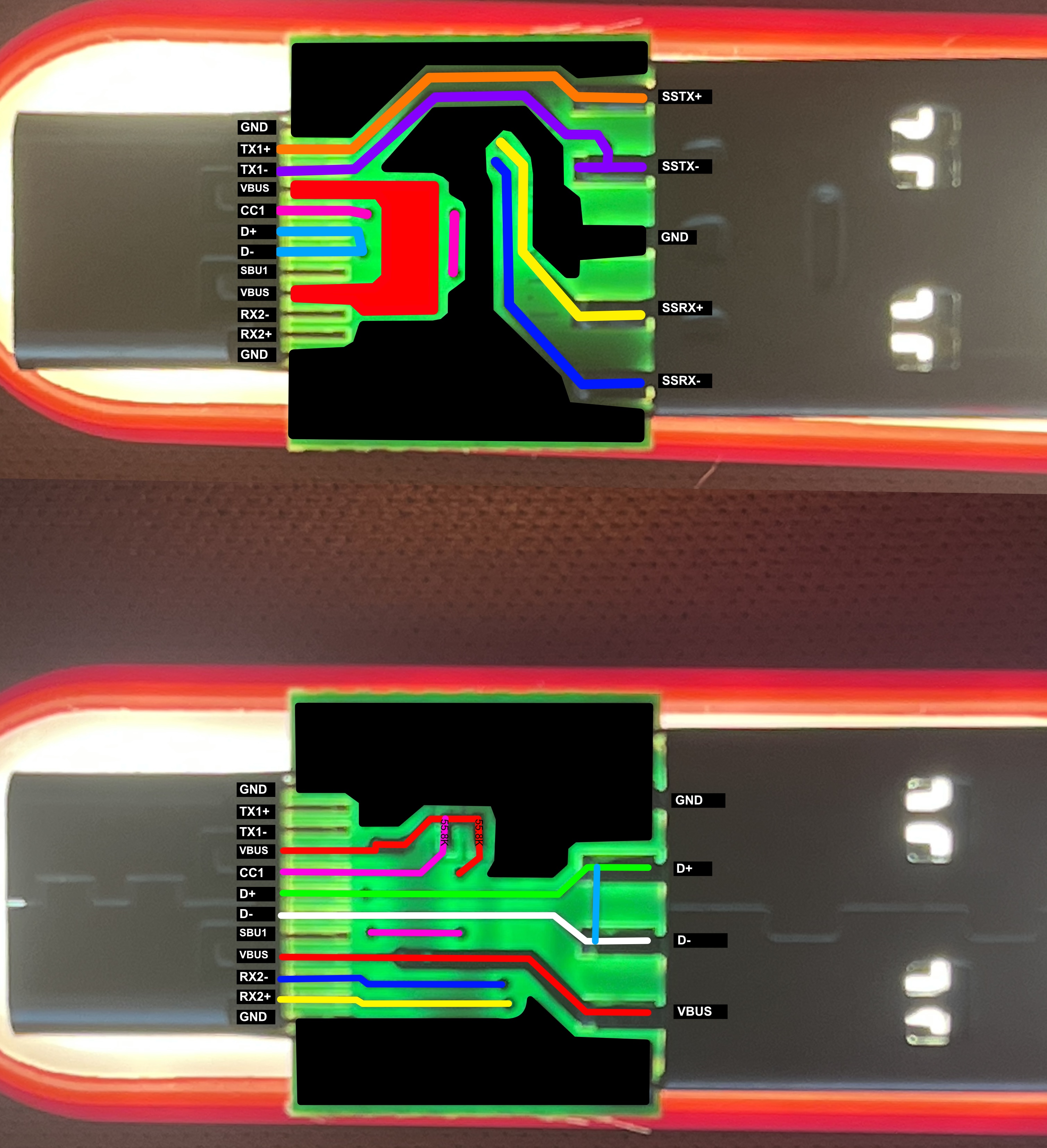
The Data Lines: D+ and D-
The USB 2.0 data lines (D+ and D-) are shorted together. This is the primary mechanism that blocks data transfer. With these lines shorted, USB enumeration cannot occur—the host computer cannot detect or communicate with any connected device as a data device.
You might wonder why these pins are connected at all, even if just shorted together. Why not leave them completely disconnected? The answer comes down to USB charging standards and device behavior. Many charging implementations, particularly older ones, use the voltage or resistance on the D+ and D- lines to detect charger capabilities and negotiate charging current. Some devices check these lines to determine if they’re connected to a dedicated charging port, a standard downstream port, or something else entirely. By shorting D+ and D- together (typically through a small resistance), the device can signal to connected hardware that this is a charging-capable port while still preventing any actual data communication. It’s a way of saying “I can provide power” without saying “I can transfer data.”
This effectively prevents USB mass storage access, HID (keyboard/mouse) emulation attacks, and any USB 2.0 data communication.
The SuperSpeed Lines: SSTX/SSRX
Interestingly, the USB 3.x SuperSpeed transmit and receive differential pairs (SSTX+/-, SSRX+/-) are connected through the device.
At first glance, this seems counterintuitive for a data blocker. However, this doesn’t compromise the data-blocking function. USB 3.x requires USB 2.0 enumeration first—all USB 3.x devices must first enumerate using the USB 2.0 protocol on the D+/D- lines before upgrading to SuperSpeed mode. With the D+/D- lines shorted, enumeration never occurs, so SuperSpeed mode is never negotiated. The Type-A connector on the host side doesn’t properly support these signals in this configuration anyway.
So why connect them at all? The USB Type-C specification expects certain pins to be present and properly terminated for correct operation. Some USB-C devices or charging protocols check for the presence of these lines as part of their cable detection or validation process. Additionally, leaving high-speed differential pairs floating (unconnected) can sometimes cause electrical issues or prevent proper USB-C negotiation. By connecting them through, even though no data can flow, the device maintains better electrical compliance with USB-C standards and avoids potential edge cases where a device might refuse to charge due to unexpected pin states.
The Critical Component: 56kΩ Resistor
The most important component for functionality is a 56kΩ resistor connecting VBUS to the CC (Configuration Channel) pin.
This resistor is mandated by the USB Type-C specification. It identifies this device as a USB Type-C power source (DFP - Downstream Facing Port), and the 56kΩ value indicates the device can supply default USB power (5V @ 500-900mA). The CC pin also determines which way the USB-C cable is plugged in. Without this resistor, a USB-C device wouldn’t recognize a valid connection and wouldn’t charge.
This is standard USB Type-C design and is necessary for the device to function as a charging adapter.
The Security Question
So, does this device do what it claims? Yes, from a purely electrical standpoint, it should effectively block data transfer while allowing charging.
But here’s the uncomfortable question: how do you verify this without destructive testing?
The sealed, opaque casing means users must trust that the manufacturer built it correctly, that no malicious components were added, that the device wasn’t tampered with in the supply chain, and that NAB properly vetted their supplier.
The internal space in these devices is more than sufficient to house a microcontroller with wireless capabilities, flash storage for malicious payloads, additional circuitry that could be activated under certain conditions, or hardware keyloggers. While the PCB I examined appeared legitimate, accepting sealed USB devices from unknown sources contradicts fundamental security principles.
The Broader Implications
This raises some interesting questions about security culture and awareness.
The distribution of these devices at CyberCon creates a teachable moment. Security professionals should be the most skeptical of unsolicited USB devices, yet the convenience of free charging adapters can override our better judgment.
Even well-intentioned organizations like NAB may not have the resources to thoroughly audit every promotional item they distribute. Supply chain attacks on hardware are notoriously difficult to detect, and most users lack the tools and knowledge to verify these devices themselves. They must either trust the vendor completely, never use the device, or destroy it for inspection (making it unusable).
Recommendations
If you’re an organization thinking about distributing USB devices, reconsider the practice entirely. In 2025, handing out USB devices at security conferences sends mixed messages about security principles. If you absolutely must do it, provide detailed specifications, PCB layouts, and verification methods. Better yet, distribute information about commercially verified products rather than branded unknowns.
For users, the advice is simple: don’t use promotional USB devices, even from trusted organizations. Buy data blockers from reputable sources with transparent supply chains. If you must use one, buy multiple from different batches and compare them. When possible, use wireless charging to avoid the USB data/power coupling entirely, or just carry your own known-good cables.
Conference organizers might want to set policies around USB device giveaways at security events, or at least provide secure, verified charging options instead. If you allow them, make it a teaching opportunity about hardware trust.
Conclusion
The NAB data blocker appears to be a legitimate, functional device that does what it claims. The electrical design is sound, using standard USB Type-C configuration with appropriate data line blocking.
However, the deeper lesson isn’t about this specific device—it’s about the principle of hardware trust. At a cybersecurity conference, we should be modeling best practices, not distributing sealed USB devices that require blind trust to use safely.
The next time someone offers you a “free” USB device, remember: in security, trust isn’t free, and sometimes the most expensive thing you can accept is a gift you can’t verify.
Disclaimer: This analysis is based on one sample device and does not constitute a comprehensive security audit. The findings suggest the device functions as advertised, but individual verification is impossible without destructive testing. Users should make their own informed decisions about using any USB device from unknown sources.